Best Border Security and Control methods.
Border Patrol Drones
What is the best method: A Wall, or Drones? In other words: fixed or a virtual border? These are not the only options. But the big question is: What do you want to achieve?
Border conflict between neighbouring nations often dominate international news headlines. Whether it be incursions in rural Africa, on the border of China and India, or Russia and East European countries or in the Middle East. Also, on the well-publicized southern border of America with the erection of “The Wall” touted by Trump.

Border Control
Border control is the set of measures taken by a state or a bloc of states to monitor its borders and regulate the movement of people, animals, and goods across the border.
Surveillance and Security is about monitoring intrusion into a controlled area. Protecting an area means monitoring for intrusions across a defined border using existing Surveillance methods.
Anatomy of Surveillance and Security
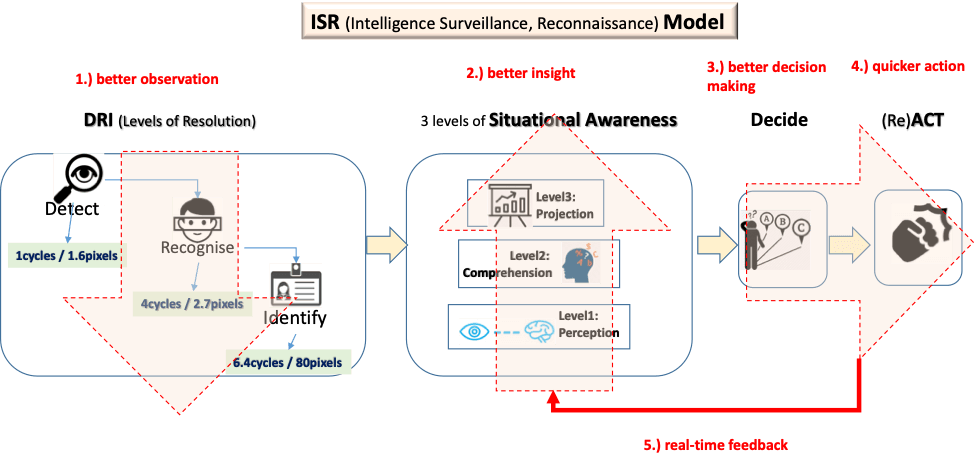
Border security and control is a subset of Surveillance and. Surveillance and security teams typically use the ISR (Intelligence Surveillance & Reconnaissance) method with which to Detect, Identify and Respond to incidents. The latter process is also known as OODA (Observe, Orient, Decide, Act).
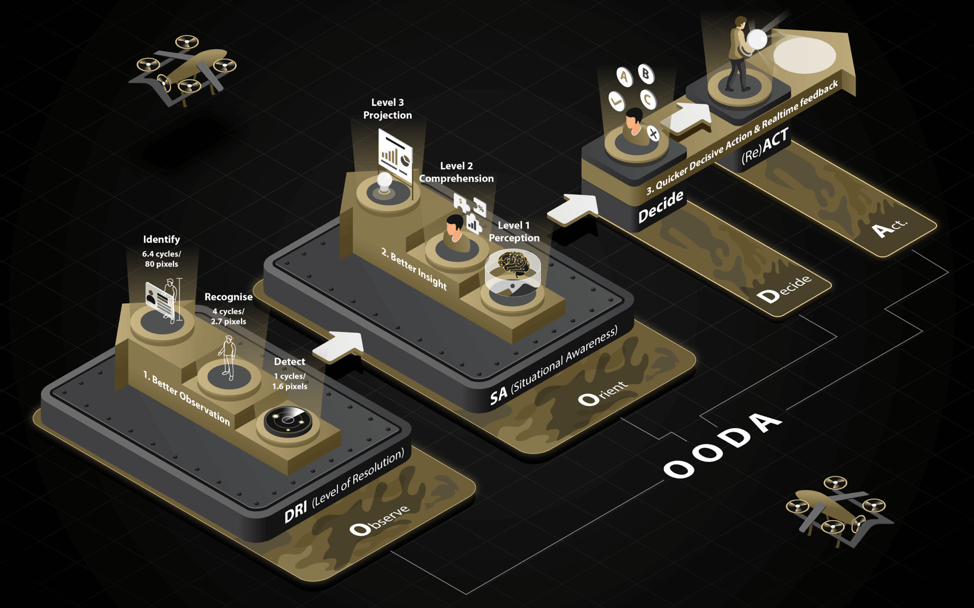
The question arises: How do various border control methods perform in respect of the ISR framework? Are they able to provide capabilities across the full ISR methodology? (Read more..)
Best Border Security and Control options
Detecting and tracking people in remote areas
A typical scenario: In the middle of the night, a ground sensor detects human footsteps in a remote area. Border personnel in an SUV head toward the area with mobile surveillance gear and night-vision goggles to locate and apprehend the intruders.
In remote areas where Border Patrol agents are widely dispersed they may depend on various types of electronic surveillance to detect and track suspicious activity until they get there. If people move out of surveillance range, agents may use drones to look for signs of human disturbance.
Many devices, technologies and personnel have to work together to prevent drugs and people from illegally entering a country. Here is a list.
Physical barriers (“the wall”)
Fixed infrastructure walls assist by delaying would-be migrants long enough to be caught. But in remote areas they are virtually useless. They are very visible encouraging people to go somewhere else. They are easy to vandalize and there also expensive to maintain. Because they are fixed, they cannot be redeployed for other purposes.
“The Wall”
One of the most publicized borders in the world is the southern border of the USA with Mexico with the construction of ex-President Trump’s border wall.

Some estimates suggest that $10 million per mile, but this does not include land acquisition, litigation, and utility relocation costs.
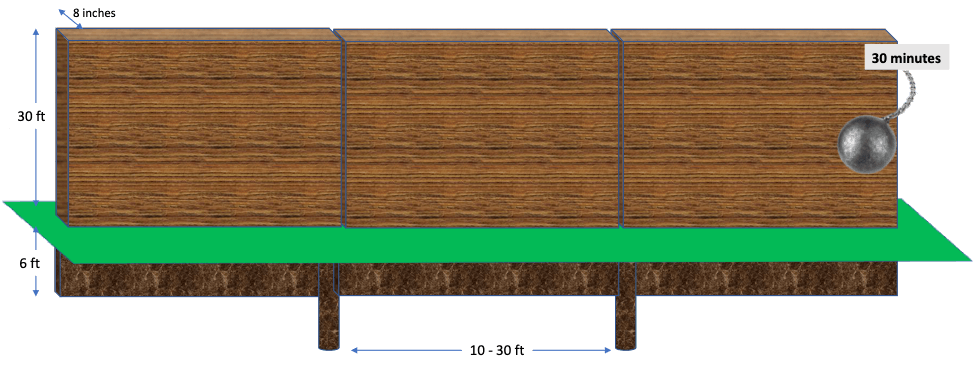
| The big question: Is it worth it? How do you evaluate the effectiveness of such a wall as a solution? Some parts of the USA/Mexico border are so remote that very few migrants are caught there. If a 500-mile section saw less than 10,000 apprehensions per year that would equate to 20 migrants per mile. If a $10 million-mile wall reduces that number by half, that would equate to $1million per migrant deterred. |
Comparative analysis
- Ground sensors are another cost-effective way of obtaining pervasive early warning alerts Buried seismic sensors, often paired with cameras, detect people and alert control center agents to observe camera footage of the area. They can be difficult to calibrate to avoid false alarms.
- Fixed aerial balloons can stay aloft for long periods and fitted with radar they can monitor areas of up to 200 miles. But they can be difficult to manage, are subject to bad weather and are also very visible.
- Towers (Fixed and/or mobile) Effective in flat, wide-open areas with up to a 6-mile observation radius, but again they very visible and easy to avoid.Mobile towers able to operate in extreme places but are not always integrated with other systems or automated, (ie, feeds need to be manually monitored).
- Manned airplanes and helicopters While expensive; can carry sophisticated surveillance equipment. Fixed-wing surveillance planes often have under-mounted infrared cameras and powerful night-vision equipment on board. If radar pings something, Air and Marine officers on board can verify what it is and follow along, alerting law enforcement on the ground.
- Satellite surveillance Another set of eyes. Expensive to use; can’t penetrate cloud cover; Satellite images are used much like images collected by other air surveillance from remote places said. Agents will compare images taken of the same location at different times to look for changes, such as evidence of new or different patterns of foot traffic. (after the fact)
- Specialized gear Agents can be faster and more effective if they have different types of on-the-go surveillance gear, such as portable radar, daytime and nighttime cameras and thermal imaging equipment that allows them to see for miles in the dark.
Drones.
Predator drones
Prior to the construction of “The Wall” the U.S. Border Patrol had already incorporated 9 unarmed Predator drones that can fly 24hr missions at altitudes of between 600m to 9000m and reach speeds of 700kmh.
At a cost of $20m each these Predator drones may be much less than the cost of the fixed wall, but has not yet the achieved the 16hrs flight time per day that it was set to achieve. Additional proposals were to extend the drone fleet by another 5 Predator drones to achieve an additional 10,000hrs of flight time per year. This equates to 1000 hours of flight time for $1m, or $1000 per hour of flight time.
Most of the deployments record video that is compared to past flights identifying changes in terrain to signal cross-border traffic allowing agencies to focus their resources effectively. This does however mean that observations are after the fact and do not provide ‘eyes on’ ISR type capability. So, these drones are really just a form of early warning system, but situational awareness and inaccessible terrain remain challenges.
Tactical Drones
Tactical drones fall into the category of sUAVs (small Unmanned Arial Vehicles) and comprise of multirotors and smaller fixed wing aircraft which often have VTOL (Vertical Take Off and Landing) capability.
These drones provide a rapid response and fast “eyes on” to the target area with live updates control stations while active waypoint tracking can be maintained based on the target parameters, like thermal signatures.
A key advantage of sUAV is its ability to collect imagery, ideally suited for reconnaissance or rapid situation awareness with application for ground force units to detect and monitor potential threats from a safe distance.
sUAVs in perimeter security do not only reduce the requirement for foot patrols by security guards, but also provide an additional oversight in instances where security guards are deployed to ensure their adherence to patrolling routines.
The speed, size, maneuverability and additional technologies make tactical drones the perfect supplement to ground security teams seeking to perform monitoring tasks more quickly and efficiently.
The 5 advantages of using tactical drones in surveillance operations:
Drones have a competitive edge over stationary cameras, as intruders can’t easily step out of sight, and they can cover areas that are normally out of reach.
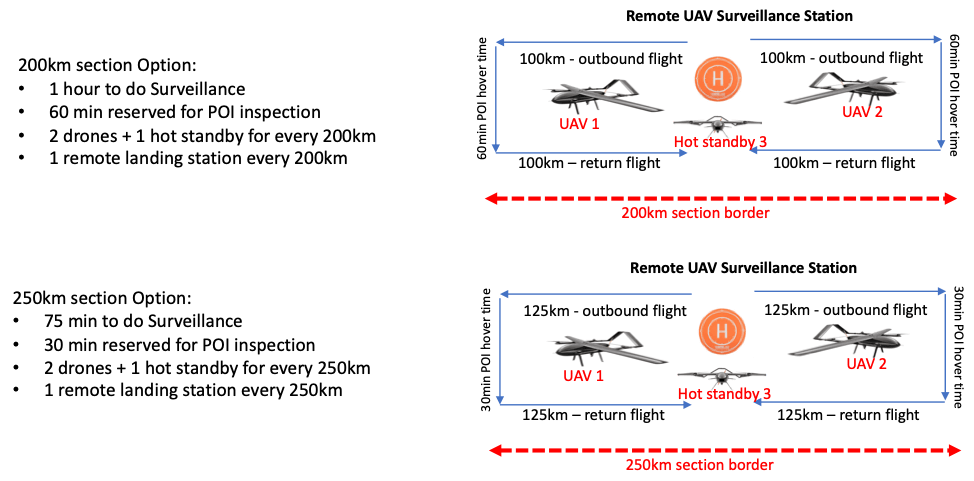
Using seismic sensors as an early warning/detection system, deploy these drones (multi-copter and smaller fixed wings) to respond to events. Where it would take border patrol agents an hour to reach a sensor 10kms away, a drone is overhead within minutes.
Deliver both Early Warning and Situational Awareness at a fraction of the cost of the Predator drones solution.
One pilot implementation suggested that this solution could secure the entire U.S.-Mexico line at a cost of $150,000 per mile.
Ddeploy drones in different configurations depending on operational requirements .
Deployment scenarios for best border security and control methods
Since 2006, huge Predator B surveillance drones have patrolled the border from above 19,000 feet, capturing and transmitting live video and detailed infrared and radar images of people on the ground.
More recently deployed smaller drones are portable, agile and quick to deploy and produce even better images, sharp enough to identify a person’s height, weight and hairstyle.
Best Border Security and Control methods: A fixed wall vs drones
Key observations:
A physical wall, once built, cannot be redeployed, or adjusted. Benefits of drones compared to a fixed wall include:
- Concentration of border management resources in priority areas
- Mobile infrastructure – move around
- Upgradeable – to later versions
- Flight missions are undeterred by geography (oceans, swamps, mountains)
- Multi-purpose (use for other purposes, ie: rescue efforts)
- Flexible virtual infrastructure, responsive to ever changing threats
- No land acquisition and litigations costs
- Drones also offer advantages across the full ISR framework from early detection to realtime feedback during execution
Perimeter security
What is Perimeter security?
Border security is another version of perimeter security which an active barrier or fortification around a defined area to prevent intrusion. It often comprises of hardware and software that generally include human guards, cameras, motion sensors, physical barriers, spot lights, and a command center.
These conventional systems have certain inherent limitations though.
- Stationary sensors such as CCTV cameras and motion detectors often have blind spots.
- Patrolling requires human guards – being on foot is inherently limiting. Patrolling can take very long and responding to incidents may be too slow to be effective.
- It is important to monitor human guards to ensure compliance to required patrolling schedules and not sleeping on the job.
Perimeter security drone
Advantages
- Drones can be rapidly deployment into areas where it would be difficult and slow to deploy a human.
- Drones are able to go to anywhere quickly and eliminate blind spots. Equipped with a thermal camera nighttime surveillance is also possible.
- A fleet of drones can automate periodical patrolling
- A drone can also track and follow an intruder providing situational awareness response teams in real-time.
- Drones can even monitor compliance of patrol guards.